Vendor Risk Management 101: Strategies for Success
Discover vendor risk management, its common risks, effective strategies, and tools to protect your business from vendor-related challenges.

Published 6 Feb 2025
Article by
7 min read
What is Vendor Risk Management (VRM)?
Vendor risk management is the proactive identification, assessment, and mitigation of risks associated with external vendors. This disciplined approach ensures that financial, operational, and reputational risks are managed systematically. Succeeding in this endeavor safeguards the company’s assets and interests and drives business continuity.
Why is Vendor Risk Management Important?
Organizations rely on third-party providers such as vendors to streamline operations and deliver top-notch services and high-quality products. However, dependence on outsourced partners introduces significant risks that could compromise the company’s vendor management system and, more importantly, the relationship they built.
Following a systematic vendor risk management process is the most effective way to minimize potential threats and their consequences. It also contributes to the following:
Increased operational efficiency – Goods and services are delivered on time in a well-managed vendor ecosystem. Aside from minimizing disruptions, demonstrating a commitment to risk prevention and mitigation builds trust with stakeholders.
Enhanced security – Through real-time tracking and rigorous assessment of vendor security practices, companies can identify potential physical and cyber security vulnerabilities, and address them immediately.
Lower financial risks – Vendor failures, inefficiencies, and outright breaches often lead to costly legal disputes and subsequent compensations. A robust vendor risk management system helps organizations avoid these problems.
Stronger compliance – A well-structured vendor risk management workflow includes selecting compliant vendors , monitoring contractual obligations, and adherence to data privacy laws . All these reduce the risk of incurring regulatory signs and penalties.
Guaranteed business continuity – A robust VRM program ensures Critical Business Functions (CBFs) won’t be compromised when faced with vendor failures or other unexpected disruptions.
Improve your GRC management
Simplify risk management and compliance with our centralized platform, designed to integrate and automate processes for optimal governance.
Common Risks in Vendor Relationships and Management
Vendor risks pose significant challenges for organizations. Poor practices lead to cascading problems throughout the operations, costing the company millions in regulatory fines, legal actions, and compensation.
Be on guard for these issues in vendor risk management examples:
Financial Risk: Cash Flow Problems
Economic downturns, poor financial planning, and changes in business priorities can compromise vendor relationships, degrade the quality of service, and disrupt supply chains.
Key Indicators to Check:
Background checks
Financial health assessments
Credit ratings
Payment history
Example:
Due diligence is non-negotiable among financial institutions, where maintaining liquidity is vital in upholding their positions. This practice prepares them for any eventuality.
Compliance Risk: Ethical Misconduct
A lax ethical environment can create a culture where improper behavior is overlooked, or worse, encouraged. This can severely damage an organization’s reputation, leading to loss of customer trust and negative publicity on top of civil laws and criminal charges.
Key Indicators to Check:
Past and current practices
Compliance status and certifications (e.g., ISO , GDPR , CCPA)
Audit outcomes
Example:
Hospitals, clinics, and similar facilities strictly select and monitor their vendors to comply with HIPAA (Health Insurance Portability and Accountability Act) regulations that protect patient privacy and health information.
Cyber Security and Data Privacy Risk: Data Breaches
According to the Cybersecurity and Infrastructure Security Agency (CISA), many organizations have experienced data breaches caused by external partners in recent years. Whether the cause is weak cyber security practices, human error, or insider threats, compromised security could lead to great financial loss, grave operational disruptions, and expensive legal liabilities.
Key Indicators to Check:
Cyber security policies and practices (e.g., encryption and firewalls)
Security audits and certifications (e.g., SOC 2)
History of breaches and system vulnerabilities
Example:
The importance of vendor risk management can’t be overstated in the continuously growing and evolving tech industry. Comprehensive VRM safeguards intellectual property, data privacy, and system security.
Operational Risk: Poor Quality Control
Consistent product and service quality is crucial for maintaining customer satisfaction, brand reputation, and long-term business success. However, vendor selection failures, insufficient oversight, and other errors in third-party risk management can lead to defects,recalls, reworks or replacements, and brand damage.
Key Indicators to Check:
Internal process documentation and quality assurance measures
Performance metrics and Service Level Agreements (SLA)
Staff qualifications
Turnover rates
Example:
In the manufacturing industry, conducting supplier audits and risk assessments is vital for product quality, supply chain reliability, and compliance with industry standards.
Reputational Risk: Negative Publicity
The vendor’s actions or associations could negatively affect the contracting company’s image. Unethical vendor performance, fraud, or environmental violations are some examples that could result in loss of trust customer trust, market positioning, and revenues.
Key Indicators to Check:
Media coverage and public perception of the vendor
Corporate Social Responsibility (CSR) practices
Ethical certifications or documented policies on Environmental, Social, and Governance (ESG)
Example:
Carefully selecting vendors, monitoring performance, and assessing risks is crucial in maintaining supply chain integrity, product quality, and brand reputation, especially in the retail sector.
Steps to Establish Effective Vendor Risk Management
VRM is essential across industries. While the specific vendor risk management procedures vary per sector, the core principles of identification, assessment, mitigation, and continuous monitoring remain consistent.
Here’s a systematic approach that ensures vendors align with the company’s operational, compliance, and security goals:
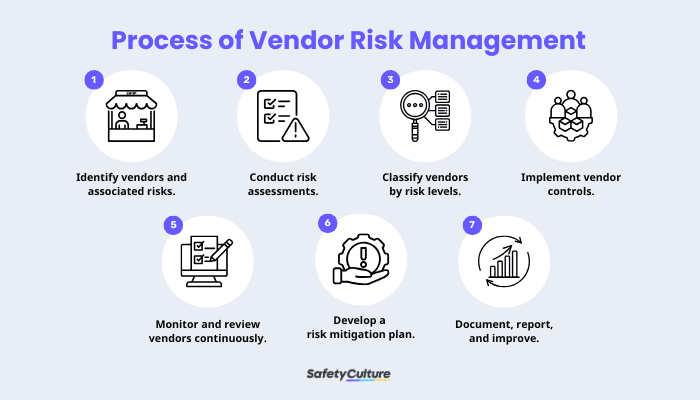
Process of Vendor Risk Management
Step 1: Identify vendors and associated risks.
The process starts by cataloging the company’s vendors to understand their role in the operations and determine the risks tied to their products or services. These are some checks to be conducted as part of due diligence:
Background checks (operational capabilities, financial stability, and security vulnerabilities)
Compliance levels
Industry and standards benchmarking
Customer and peer reviews
Step 2: Conduct risk assessments.
Create vendor risk management metrics based on factors reviewed during the due diligence (e.g., operational criticality, data access, compliance with regulations, and geographic risks). Use industry-standard frameworks to guide assessments, ensuring accuracy, clarity, and reliability of results.
Create your own Vendor risk assessment checklist
Build from scratch or choose from our collection of free, ready-to-download, and customizable templates.
Step 3: Classify vendors by risk levels.
Categorize vendors into high, medium, or low-risk tiers, based on their impact on the business. This helps prioritize risk management efforts, ensuring critical vendors receive more scrutiny and frequent monitoring.
Step 4: Implement vendor controls.
Establishing measures to mitigate risks is arguably the most crucial part of the vendor risk management framework because this is where identified risks are confronted head-on. Here are some examples of controls often implemented across industries:
Contractual – SLAs, Data Protection Agreements (DPAs), and insurance coverages
Security – Strong access controls, data encryption, and incident response plans
Operational – Communication methods, Business Continuity Planning (BCP) , third-party risk management programs
Step 5: Monitor and review vendors continuously.
Continuously track vendor performance and risk factors to stay ahead of potential issues. These are some vendor risk management best practices under this step:
Schedule periodic reviews and audits to verify compliance and performance.
Foster open communication with vendors for transparency.
Automate vendor risk management, utilizing software solutions to streamline information sharing and drive collaboration.
Step 6: Develop a risk mitigation plan.
Prepare for potential vendor-related disruptions based on identified risks by developing an incident response plan. It should detail the corrective measures, a resolution timeline, and the personnel responsible for handling the issue. Be ready to transition to alternative vendors, if necessary.
Step 7: Document, report, and improve the VRM program.
Risk management reporting and comprehensive documentation uphold accountability and transparency, especially for compliance audits. This also informs future decision-making to improve the organization’s VRM efforts.
Effectively Manage Vendor Risks with SafetyCulture
Why Use SafetyCulture?
SafetyCulture is a mobile-first operations platform adopted across industries, such as manufacturing, mining, construction, retail, and hospitality. It’s designed to equip leaders and working teams with the knowledge and tools to do their best work—to the safest and highest standard.
Streamline workflows by automating vendor risk assessments and centralizing monitoring to ensure the early identification and mitigation of vendor risks and adherence to regulatory and contractual requirements. Foster a culture of accountability and transparency to enhance risk management practices through a unified platform.
✓ Save time and reduce costs ✓ Stay on top of risks and incidents ✓ Boost productivity and efficiency ✓ Enhance communication and collaboration ✓ Discover improvement opportunities ✓ Make data-driven business decisions
Related articles
Food Safety
Safety

A Comprehensive Guide to Natasha’s Law Training
Learn about the process of Natasha’s Law training and how it helps food businesses efficiently meet allergen labeling requirements.
Construction Safety
Safety

A Complete Guide to Scaffolding Safety Training
Learn everything about scaffolding safety training, from topics to best practices, to uphold construction and maintenance safety.
Construction Safety
Safety

A Simple Guide to Oil and Gas Production
Learn about the oil and gas production process and the equipment and modern technologies used to improve field productivity.