What is a Security Risk Assessment?
A security risk assessment is a process that helps organizations identify, analyze, and implement security controls in the workplace. It prevents vulnerabilities and threats from infiltrating the organization and protects physical and informational assets from unauthorized users.
Requirements
A security risk assessment is a continuous process that allows the organization to monitor and update the current snapshot of threats and risks to which it might be exposed. It is a requirement for different compliance standards, including the following:
- Payment Card Industry Data Security Standards (PCI-DSS) – An information security standard for organizations that handle branded credit cards from the major card schemes.
- International Organization for Standardization (ISO) 27001 – An internationally recognized set of guidelines that focuses on information security and provides a framework for the Information Security Management System (ISMS).
- Health Insurance Portability and Accountability Act (HIPAA) – a US law that requires the careful handling of Protected Health Information (PHI) or individually identifiable health information.
Improve your GRC management
Simplify risk management and compliance with our centralized platform, designed to integrate and automate processes for optimal governance.
Explore nowWhy Perform a Security Risk Assessment?
Conducting risk assessments for cybersecurity helps prevent potential threats that could compromise the security of an organization. Security officers should understand the relationships between security components, including threats, vulnerabilities, and risks, to secure the organization from physical, socio-economic, and environmental threats. It further helps an organization to:
- prevent any potential dangers that have the capability, motivation, and intent to exploit existing vulnerabilities;
- protect valuable and sensitive company data, including personal and financial information from ransomware and data loss;
- comply with regulatory standards to prevent lawsuits;
- measure the risk ranking for each asset and assess criticality based on how it would affect business operations; and
- secure the company’s reputation and brand image.
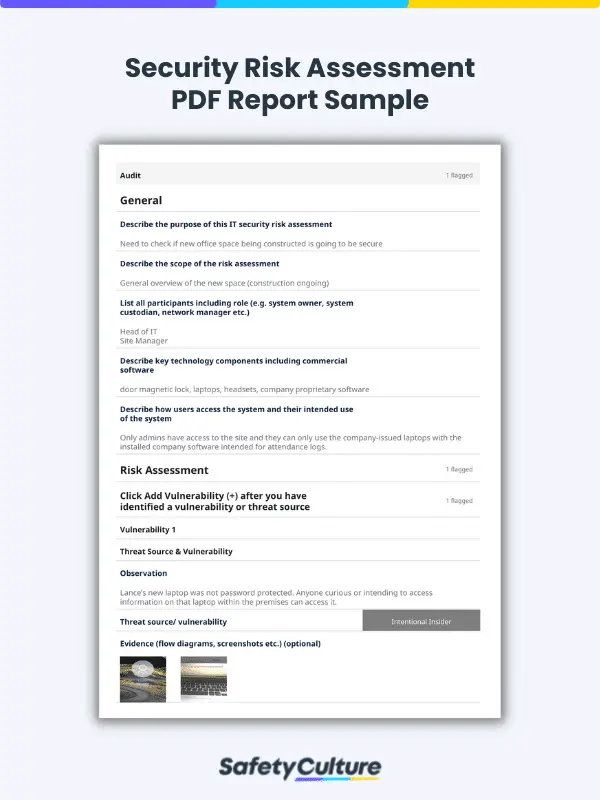
Security Risk Assessment PDF Report Sample | View Template
Examples
Performing risk assessments is a crucial task for security officers. It is a far-reaching review of anything that could pose a risk to the security of an organization. The following 3 categories of security controls with examples can help provide a better understanding of the scope of security in business operations.
1. Management Security Control
Management security or administrative control is the overall design of controls that provides guidance, rules, and procedures for implementing a security environment. It safeguards the organization from data corruption and unauthorized access by internal or external people and protects the company from financial loss, reputational damage, consumer confidence disintegration, and brand erosion.
Example: The organization identifies a risk of unauthorized access to sensitive data stored on an internal database server. The management security control team is responsible for defining who is authorized to access the data.
2. Operational Security Control
Operational security or technical control defines the effectiveness of controls. It includes access authorities, authentication, and security topologies applied to applications, networks, and systems.
Example: The organization identifies a risk of unauthorized access to sensitive data stored on an internal database server. IT teams use operational security control to prevent and detect unauthorized server login.
IT managers can use a cybersecurity assessment checklist or IT risk assessment checklist to help identify malicious activities and implement needed measures to manage threats. It helps validate the consequence, likelihood, and risk rating of identified vulnerabilities.
3. Physical Security Control
Physical security control is the protection of personnel and hardware from tangible threats that could physically harm, damage, or disrupt business operations.
Example: The organization identifies a risk of unauthorized access to sensitive data stored on an internal database server. The organization can apply physical security controls to restrain visitors and unauthorized personnel to access restricted areas.
Facility security officers (FSO) can use a facility security assessment checklist to carry out an extensive internal scan of the facility’s infrastructure, vulnerabilities, and potential threats. It helps assess the building security condition to protect occupants from the possibility of higher risks.
Create Your Own Security Risk Assessment Checklist
Eliminate manual tasks and streamline your operations.
Get started for FREEHow to Carry Out a Security Risk Assessment
The process for assessing security risks varies depending on the needs of a company. It relies on the type of business operation, assessment scope, and user requirements. Generally, it can be conducted with the following steps.
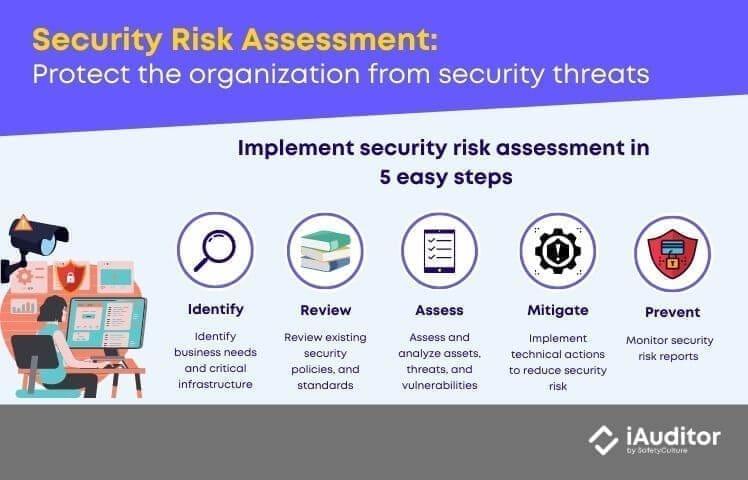
5 Steps to Implement Security Risk Assessment
Step 1: Identify
- Identify the business needs and critical assets of technology infrastructure that may affect the overall IT and security direction.
Step 2: Review
- Review existing security policies, standards, guidelines, and procedures and diagnose sensitive data that is created, stored, or transmitted by technology infrastructure assets.
Step 3: Assess
- Assess and analyze assets, threats, and vulnerabilities including their impact, likelihood, and risk rating.
- Check the physical protection applied to computing equipment, server, and other network components.
- Conduct technical and procedural review and investigation of network architecture, protocols, and other components to ensure it is implemented according to security policies.
- Review and assess configuration, implementation, and usage of remote access systems, servers, firewalls, and other external network connections.
- Check access control systems for authorized users and other authentication policies.
- Check physical assets including access cards for staff and visitors.
- Check the perimeter protection and inspect the operational condition of CCTV cameras and alarm systems.
- Ensure housekeeping is properly observed.
Step 4: Mitigate
- Review and analyze assessment reports and determine how to effectively allocate time and resources towards risk mitigation.
- Implement technical actions to address the vulnerabilities identified and reduce the level of security risk.
- Assign corrective actions and recommendations to appropriate personnel to enforce security controls for each risk.
Step 5: Prevent
- Conduct regular security assessments, monitor updates, and communicate risk assessment reports to an authorized person.
- Streamline reporting processes to minimize threats and vulnerabilities from occurring.
Training
Creating a culture of safety in the workplace is more than just a legal requirement or a box to check. As an employer, it’s your responsibility to build a workplace where people feel safe, valued, and motivated to do their best work.
Security risk assessment training is a set of informational lessons to help employees develop skills for identifying, analyzing, and evaluating security risks. It is important to invest in this type of training to help your organization stay safe in the digital space, as cybersecurity awareness training can serve as the starting point for empowering workers with a clearer understanding of security risks. For example, this free online training course contains the basics of the most common cyber attacks and how people can protect themselves.
Tool
Technological growth comes with the transformation of security threats. Lawbreakers discover new mechanisms to break through the most stringent security systems. A security risk assessment helps protect the organization and building occupants from possible exposure to threats that can sabotage their assets and expose them to much higher risks.
Traditionally, risk assessments are performed with the use of pen and paper that is susceptible to deterioration and loss. It takes a lot of time to hand over assessment reports, which increases the chances of exposing the organization to security risks. SafetyCulture (formerly iAuditor) is a mobile inspection app that can help security officers proactively identify security risks and respond on time to mitigate the risks.
Security Risk Assessment Software
To ensure the effectiveness of security risk evaluations the following SafetyCulture features can help security officers save time conducting assessments and handover of security risk reports.
Conduct risk assessments anytime, anywhere on a mobile device
SafetyCulture makes it easy for anyone on the team to conduct inspections and audits on the go. Whether online or offline SafetyCulture can record assessment results in real-time that are automatically saved securely in the cloud.
Turn security issues into actions
Create corrective actions on the spot for identified security threats. Set the due date and priority level, then assign them to the authorized personnel to address and mitigate security risks immediately.
Review performance and trends
Automatic syncing between mobile devices and desktop platform provide real-time analytics dashboards on Premium accounts. Get instant visibility on identified security issues and team productivity.
Performing regular security assessments is vital to keep a protected and up-to-date security system. Here are other features of SafetyCulture that could help improve risk assessment performance and monitoring:
- capture unlimited photo evidence, annotate, and add notes to further explain the issue;
- round-the-clock handover of reports even right after conducting the assessment;
- easy to set schedules and notifications to never miss an expected assessment; and
- free use for small security teams and can be upgraded with unlimited reports and storage for Premium accounts.




