Security Risk Assessment
Learn about security risk assessment, why organizations need to perform it, the categories of security control, and how to carry out a risk assessment.

Published 14 Nov 2025
Article by
6 min read
What is a Security Risk Assessment?
A security risk assessment is a process that helps organizations identify, analyze, and implement security controls in the workplace. It prevents vulnerabilities and threats from infiltrating the organization and protects physical and informational assets from unauthorized users.
Regulations and Standards
A security risk assessment is a continuous process that allows the organization to monitor and update the current snapshot of threats and risks which it might be exposed to. It’s a requirement for different compliance standards, including the following:
Payment Card Industry Data Security Standards (PCI-DSS) – An information security standard for organizations that handle branded credit cards from the major card schemes.
International Organization for Standardization (ISO) 27001 – An internationally recognized set of guidelines that focuses on information security and provides a framework for the Information Security Management System (ISMS).
Health Insurance Portability and Accountability Act (HIPAA) – a US law that requires the careful handling of Protected Health Information (PHI) or individually identifiable health information .
Improve your GRC management
Simplify risk management and compliance with our centralized platform, designed to integrate and automate processes for optimal governance.
Security Risk Assessment Examples
Performing risk assessments is a crucial task for security officers. It’s a far-reaching review of anything that could pose a risk to the security of an organization. The following categories of security controls, with examples, can help provide a better understanding of the scope of security in business operations:
Management Security Control
Management security or administrative control is the overall design of controls that provides guidance, rules, and procedures for implementing a security environment. It safeguards the organization from data corruption and unauthorized access by internal or external people and protects the company from financial loss, reputational damage, consumer confidence disintegration, and brand erosion.
Example: The organization identifies a risk of unauthorized access to sensitive data stored on an internal database server. The management security control team is responsible for defining who is and isn’t authorized to access the data.
Operational Security Control
Operational security or technical control defines the effectiveness of controls. It includes access authorities, authentication, and security topologies applied to applications, networks, and systems.
Example: The organization identifies a risk of unauthorized access to sensitive data stored on an internal database server. IT teams use operational security controls to prevent and detect unauthorized server login.
A cybersecurity assessment checklist can help IT managers identify malicious activities and implement needed measures to manage threats. It helps validate the consequence, likelihood, and risk rating of identified vulnerabilities.
Physical Security Control
Physical security control is the protection of personnel and hardware from tangible threats that could physically harm, damage, or disrupt business operations.
Example: The organization identifies a risk of unauthorized access to sensitive data stored on an internal database server. The organization can apply physical security controls to restrain visitors and unauthorized personnel from getting to restricted areas.
Facility security officers (FSO) can use a facility security assessment checklist to carry out an extensive internal scan of the facility’s infrastructure, vulnerabilities, and potential threats. It helps assess the building security condition to protect occupants from the possibility of higher risks.
How Do You Perform a Security Risk Assessment?
The process for assessing security risks varies depending on the needs of a company. It relies on the type of business operation, assessment scope, and user requirements. Generally, it can be conducted with the following steps.
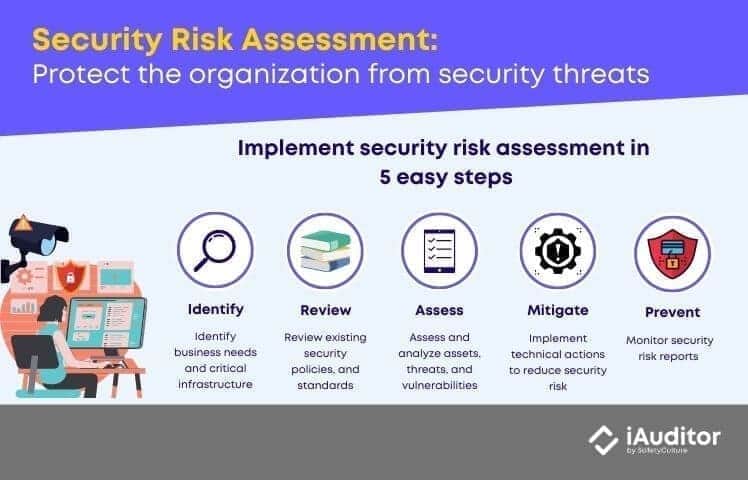
5 Steps to Implement Security Risk Assessment
Step 1: Identify
Spot your organization’s business needs and determine the critical assets within your technology infrastructure. Include data, software systems, hardware, and intellectual property that are essential to business operations. Define what needs protection to align your assessment with the overall IT and security direction. Prioritize high-value assets to determine which areas require the most rigorous security measures.
Create your own Security Audit checklist
Build from scratch or choose from our collection of free, ready-to-download, and customizable templates.
Step 2: Review
Examine all existing security policies, standards, guidelines, and procedures. Establish a baseline understanding of your organization’s current security posture and identify gaps or outdated practices. Diagnose and document all sensitive data that is created, stored, or transmitted across your technology infrastructure. Focus on the most vulnerable and high-risk areas by understanding how sensitive data moves within your systems. Ensure compliance with applicable regulations and industry standards by updating and refining your policies regularly.
Step 3: Assess
Assess and analyze all assets, threats, and vulnerabilities to determine their potential impact, likelihood, and overall risk rating. Check the physical protection of computing equipment, servers, and network components to confirm they are secure. Conduct technical and procedural reviews of network architecture, configurations, and external connections to verify compliance with security policies and detect weak points.
Inspect access control systems to ensure only authorized users gain entry, and audit physical assets such as access cards for proper use. Evaluate perimeter protections, including CCTV cameras, alarm systems, and entry points, to confirm they function correctly. Maintain good housekeeping practices to promote safety, organization, and an environment that minimizes the chance of security breaches.
Step 4: Mitigate
Review and analyze all assessment reports to determine how to allocate time, budget, and resources effectively for addressing vulnerabilities. Implement technical and procedural measures that reduce identified risks, such as applying patches, strengthening access controls, or updating firewall configurations.
Assign corrective actions and recommendations to responsible personnel to ensure accountability and proper follow-up. Enforce security controls tailored to each identified risk to improve protection and enhance resilience against future threats. Integrate mitigation activities into your organization’s continuous security improvement cycle to maintain long-term defense readiness.
Step 5: Prevent
Conduct regular security assessments to identify emerging threats and address them proactively. Monitor system updates, infrastructure changes, and threat intelligence to detect and resolve potential vulnerabilities before they escalate. Communicate risk assessment findings and reports to authorized stakeholders to support informed decision-making and continuous improvement. Streamline reporting and incident management processes to enhance responsiveness, minimize recurring issues, and foster a culture of awareness and prevention across the organization.
Efficiently Manage Security Risks with SafetyCulture
Why Use SafetyCulture?
Why Use SafetyCulture?
SafetyCulture is a mobile-first operations platform adopted across industries such as manufacturing, mining, construction, retail, and hospitality. It’s designed to equip leaders and working teams with the knowledge and tools to do their best work—to the safest and highest standard.
Promote a culture of accountability and transparency to strengthen your organization’s security risk assessment process. Encourage every team member to take ownership of their security responsibilities and actions. Align governance practices, enhance risk management protocols, and ensure compliance with legal requirements and internal policies. Streamline and standardize assessment workflows through a unified platform to achieve consistent, efficient, and compliant security management.
✓ Save time and reduce costs
✓ Stay on top of risks and incidents
✓ Boost productivity and efficiency
✓ Enhance communication and collaboration
✓ Discover improvement opportunities
✓ Make data-driven business decisions
FAQs About Security Risk Assessments
Related articles
Environmental Safety
Safety

Stormwater Pollution Prevention Best Management Practices
Learn about the types of best management practices for SWPP and the steps to effectively implement them in prevention plans.
Construction Safety
Safety

Understanding Mechanical Excavation in Modern Construction
Learn about mechanical excavation and how to maintain safety across excavation projects with this guide.
Risk Assessment
Safety

Disaster Recovery Policy: The Ultimate Guide
Discover how a disaster recovery policy bolsters operational resilience and safety through clear procedures and continuous improvement.