Published 26 Sept 2025
Article by
5 min read
What is a Network Audit Checklist?
A network audit checklist is a tool used during routine network audits to help identify threats to network security, determine their source, and address them immediately. A network audit checklist is typically used for checking the firewall, software, hardware, malware, user access, network connections, etc.
What is a Network Security Audit?
A network security audit, performed at least once a year, is the process of proactively assessing the security and integrity of organizational networks. These audits are conducted by IT managers and network security teams to uncover and mitigate costly threats to an organization’s network and data assets.
5 Common Network Security Risks and Recommended Solutions
As network security risks continue to evolve, they remain a constant threat to any organization. Here are some of the most common network security risks and the recommended solutions to mitigate them:
Malware
Malware, such as computer viruses, spyware, trojans, worms, etc., are constant threats to the network and other information technology assets. Always check if anti-malware is updated and is running periodic scans to protect the organization’s assets from potential threats.
Outdated operating systems
System updates include patches and updated security measures that intend to protect assets from newly discovered vulnerabilities. Allowing applicable system updates will help ensure that your operating systems and assets are protected from new threats.
New threats
Organizations that were vulnerable got hit in 2018 by the NotPetya ransomware, losing hundreds of millions of dollars and suffering unscheduled operational downtime. Proactively staying up-to-date with new threats to cyber and network security can help organizations mitigate IT risks and avoid reputation-damaging losses.
Unauthorized access
Employees and vendors who are no longer associated with the organization but still have access to company assets can be network-security risks. Proper off-boarding and deactivation of access will help protect the network from unintended or malicious access.
Human error
Neglect, lack of knowledge of network security, and malicious intent can render a network vulnerable to security threats. Provide training in using information technology and network assets for all employees and remind everyone to be mindful of how they handle information and network security. Conducting network security audits can help proactively reinforce cybersecurity and avoid costly IT incidents.
What to Include in a Network Audit Checklist
Network audits and assessments vary and can be modified depending on the organization’s specifications. The following elements, however, are some of the most important ones that should be checked when performing a network audit:
Firewall – Check firewall configurations, rules, and logs to ensure unauthorized traffic is blocked and policies are up to date. It should also include instructions on how to best create a password for the firewall to avoid unwanted logs.
Computers and network devices – Inspect all endpoints, including computers, routers, and Wireless Access Points (WAPs) for proper configuration, connectivity, and security.
User accounts – Review user access levels, disable inactive accounts, and ensure strong authentication practices are in place.
Malware protection – Verify that malware protection software is installed, updated, and actively monitoring all devices.
Software patch management – Make sure that operating systems and applications are regularly updated with the latest security patches and updates.
How to Conduct a Network Security Audit: A Step-by-Step Guide
Here’s a concise guide on how to perform a network audit to ensure a secure system, broken into actionable steps:
Define the scope – Identify which parts of the network to audit—e.g., internal systems, remote connections, cloud infrastructure, etc. Set goals and outline any compliance requirements (e.g., HIPAA, PCI-DSS).
Gather network information – Map out the network architecture, including all devices, users, applications, IP addresses, and connections.
Review security policies – Evaluate existing security policies for password management, access controls, acceptable use, and incident response procedures.
Check user access controls – Audit user accounts, roles, and permissions. Ensure users only have access to what they need (principle of least privilege).
Assess hardware and software security – Examine routers, firewalls, switches, endpoints, and servers. Ensure firmware is updated and unused services are disabled.
Evaluate malware and threat protection – Verify that antivirus, anti-malware, and endpoint protection solutions are installed, updated, and properly configured.
Inspect firewall and intrusion detection settings – Review firewall rules, access control lists (ACLs), and logs. Ensure intrusion detection/prevention systems (IDS/IPS) are active.
Test for vulnerabilities – Use automated scanning tools and manual testing to identify vulnerabilities in devices, software, and configurations.
Check patch management – Confirm that all systems are regularly updated with the latest security patches and software updates.
Generate an audit report – Document findings, highlight vulnerabilities, and recommend remediation steps. Prioritize issues by risk level.
Implement improvements – Fix vulnerabilities, update configurations, and adjust security policies as needed based on the audit results.
Schedule regular audits – Set a recurring schedule for future audits to maintain security posture and stay ahead of potential threats. Use digital network audit checklists to ensure you won’t miss essential items to look into.
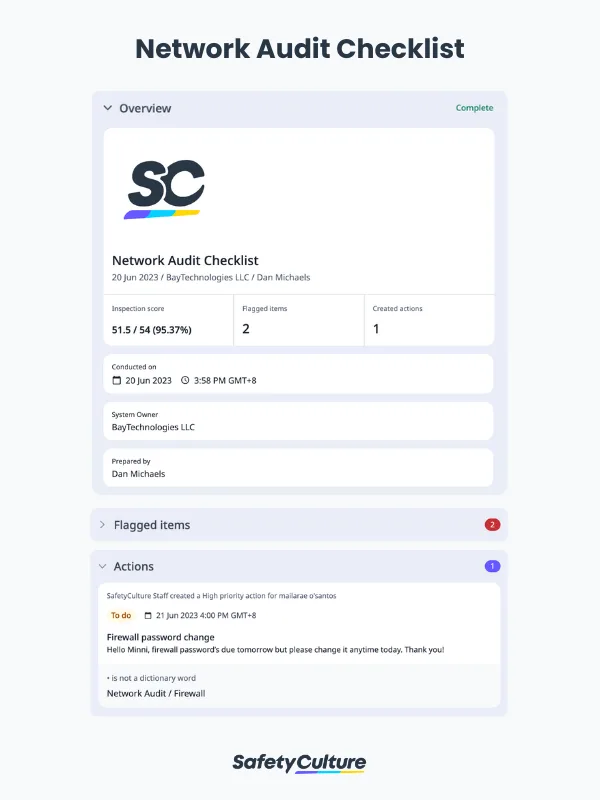
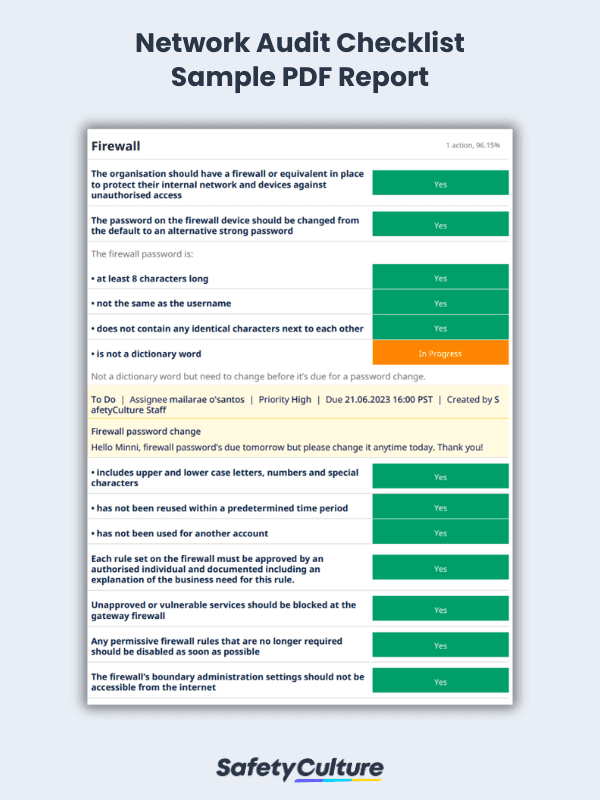
Network Audit Checklist PDF Report
To give you an overview of the report, here’s a look at a completed network audit in a PDF format:
Still looking for a checklist?
Search, filter, and customize 60,000+ templates across industries and use cases.