Published 8 Mar 2024
Article by
3 min read
What is a Vendor Risk Assessment?
A vendor risk assessment is an evaluation tool used by organizations to understand and reduce the risks that come with working with third-party vendors of products or services. When purchasing or working with third-party vendors, organizations are left vulnerable to various risks such as security breaches, business interruption, reputational damage caused by vendor’s non compliance with regulation and industry standards, and more. To prevent those from happening, a vendor risk assessment should be done to identify and evaluate the risks and hazards of working with a third-party vendor. It is done through a series of questions that thoroughly evaluates their ability to meet the requirements set by the organization (i.e., accountability, timeliness, completeness, quality of goods or service, etc). Vendor risk assessments also allow organizations to implement efficient methods of vendor onboarding, and monitor and measure their performance.
What is Vendor Risk Assessment Checklist?
A vendor risk assessment checklist is a tool used by procurement officers to assure vendor compliance with regulatory requirements such as data privacy,due diligence, and security risks. It is a crucial process in vendor management that helps to scrutinize product cost, service delivery, and software demonstrations.
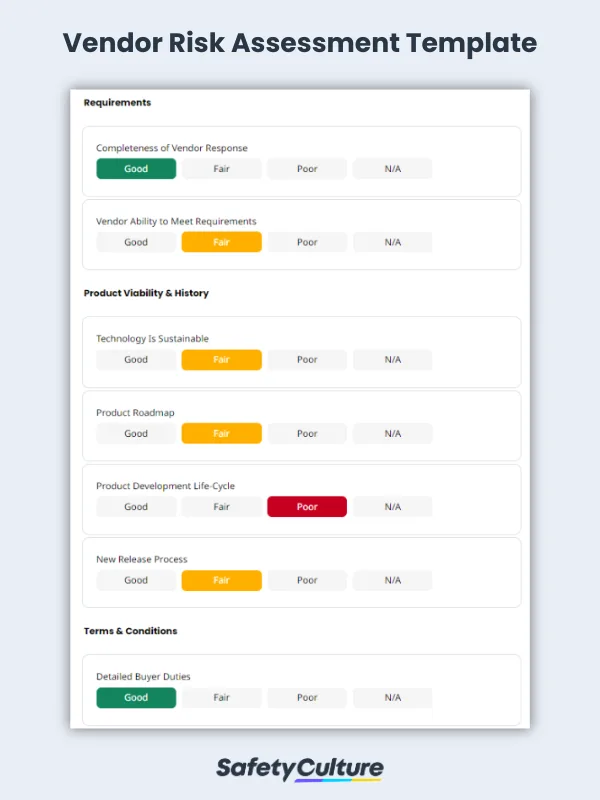
Vendor Risk Assessment Checklist
Common items a vendor risk management plan will consider:
Vendor assessment
Adherence to organizational standards
Company information
Project understanding
Requirements
Product viability & history
Terms & conditions
Vendor software demonstration
What is Vendor Risk Management Program?
Vendor Risk Management (VRM) is the process of choosing appropriate partners that adhere to organizational needs and ensuring that vendor deficiencies do not result in costly business disruptions. Having a program for vendor risk management also prevents other adverse effects such as regulatory sanctions, financial losses, and business closures.
What is Vendor Security Risk Assessment?
A vendor security risk assessment determines how a vendor handles confidential information and asset management and what security controls they have in place in case of threats, vulnerabilities, and other security breaches that can put data at risk. Evaluate the effectiveness of the vendor’s incident, environmental, organizational and human resource security to check their compliance with your organization’s policies and other relevant regulations.
How Do You Do a Vendor Risk Assessment?
Conduct a vendor security risk assessment and perform the following steps to ensure that the overall vendor risk assessment is complete and ready for use as part of your organization’s VRM program:
Step 1: Conduct a background check to ensure vendors can produce and maintain a high-quality standard without causing any risk to both the company and its customers.
Step 2: Gauge a vendor’s reliability and accuracy to produce the expected output, so as to avoid financial losses and hindrances to business operations.
Step 3: Check feedback, reviews, and press releases from a vendor’s previous clients to determine their credibility.
Step 4: Evaluate how a vendor manages data documentation and disaster plans throughout the project cycle.
Step 5: Identify a vendor’s preparation and remediation plans in case of unexpected incidents such as accidents, disasters, and data loss.
Step 6: Check for the functionality of retrieval processes, access controls, and backup plans.