Understanding the Essence of Cybersecurity Governance to Organizations
Learn about the importance of cybersecurity governance in establishing robust frameworks to safeguard digital assets and navigate cyber threats.

Published 30 Oct 2024
Article by
7 min read
What is Cybersecurity Governance?
Cybersecurity governance (sometimes spelled as cyber security governance) refers to the set of policies, processes, and practices that organizations implement to ensure the effective management, protection, and oversight of their information systems and digital assets. It establishes a structured framework to address cybersecurity risks, compliance requirements, and the evolving threat landscape.
Governance in cybersecurity is essential for organizations of all sizes and industries, from small businesses to enterprises. It emphasizes a strategic, risk-based approach to cybersecurity, recognizing that it’s a critical aspect of overall business governance.
Why is Cybersecurity Governance Important to Organizations?
As technology becomes more integral to business operations, organizations face an unprecedented reliance on information technology, accompanied by an escalating threat landscape. Cybersecurity governance serves as the backbone of an organization’s defense against cyber threats, providing a set of strategies to safeguard sensitive information, uphold regulatory compliance, and ensure the continuity of business operations.
Apart from those, the following are some aspects wherein cybersecurity governance plays a key role:
Protection of Sensitive Information
By upholding the principles of confidentiality, integrity, and availability (CIA), governance measures ensure that unauthorized access to critical data is prevented, data integrity is maintained, and information remains accessible when needed. Robust controls and encryption mechanisms implemented through governance frameworks create a fortified barrier against cyber threats, shielding the organization’s sensitive information from potential breaches and data compromises.
Risk Management and Mitigation
Through regular risk assessments, governance frameworks enable organizations to identify vulnerabilities early on so that they can implement timely and effective technological risk mitigation strategies. This strategic focus on risk management not only strengthens an organization’s overall cybersecurity posture but also minimizes the potential impact of cyber threats on its operations, reputation, and financial well-being.
Legal and Regulatory Compliance
By closely aligning with relevant laws and regulations, governance frameworks help organizations avoid legal repercussions and financial penalties. Also, adherence to industry standards demonstrates a commitment to ethical practices, reinforcing the organization’s credibility and maintaining a positive standing within its regulatory environment.
Preservation of Business Continuity
Through the development of incident response plans, governance frameworks enable organizations to react swiftly and cohesively in the face of cybersecurity incidents. By minimizing downtime, data loss, and financial impact, these plans ensure that business operations can continue seamlessly, safeguarding an organization’s resilience in the event of unexpected cyber threats.
Customer and Stakeholder Trust
Organizations that demonstrate a commitment to robust cybersecurity measures through effective governance practices instill confidence in their clients and partners. This trust, in turn, becomes a valuable asset, enhancing the organization’s reputation and fostering long-term, positive relationships with customers and stakeholders.
Principles
Cybersecurity governance is guided by a set of principles that organizations should abide by to establish effective and resilient security measures. The following serve as foundational elements for developing a comprehensive cybersecurity governance framework:
Risk-Based Approach — allows organizations to prioritize efforts based on the potential impact and likelihood of threats
Alignment with Business Objectives — ensures that security measures support and enhance the organization’s mission and values
Proactive Protection — includes proactive monitoring, vulnerability management, and secure-by-design practices
Comprehensive Policies and Procedures — cover all aspects of information security
Continuous Monitoring and Adaptation — enables timely detection and response to cybersecurity incidents in real-time
Governance Structure and Accountability — ensures accountability at all levels of the organization
Regulatory Compliance — allows updated knowledge of relevant laws, regulations, and industry standards related to information security
Education and Training — helps enhance employees’ understanding of cybersecurity best practices
Incident Response Readiness — minimizes potential damage and downtime
Performance Metrics and Reporting — facilitates informed decision-making based on Key Performance Indicators (KPI) tracking
Common Challenges
Managing and maintaining cybersecurity governance comes with its challenges, given its complexity. These are mainly attributed to how organizations face various issues requiring strategic solutions to ensure their cybersecurity measures are effective and resilient.
Most commonly, the following are some examples of such issues and challenges they may encounter:
Rapidly Evolving Threat Landscape
Cyberattackers continually develop new tactics, techniques, and procedures (TTPs), making it challenging for organizations to anticipate and defend against emerging threats. Staying ahead of these evolving risks requires proactive risk management, continuous monitoring, and the ability to adapt governance measures promptly.
Balancing Security and Business Objectives
Organizations need to implement security controls without hindering operational efficiency or innovation. Striking the right balance involves aligning security policies with the organization’s strategic goals, ensuring that cybersecurity measures support rather than hinder business processes.
Shortage of Skilled Cybersecurity Professionals
As the demand for cybersecurity expertise grows, many organizations struggle to attract and retain qualified professionals. This shortage can impact the effective implementation of cybersecurity governance programs, as organizations may face difficulties in developing and maintaining a skilled team capable of addressing evolving threats and challenges.
7 Steps in Building a Cybersecurity Governance Program
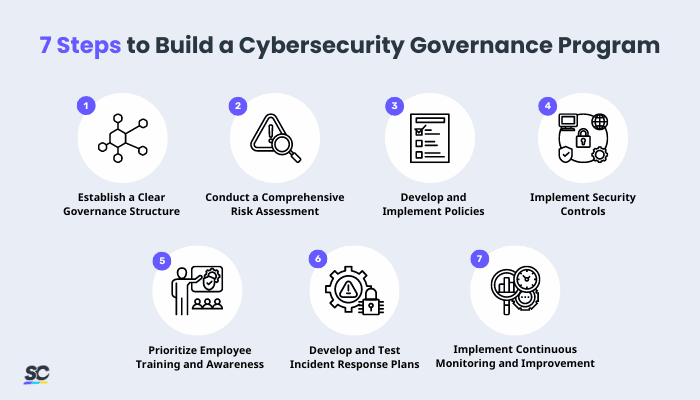
7 Steps to Build a Cybersecurity Governance Program
To guide organizations in developing and maintaining an effective cybersecurity governance program, here are 7 steps to follow to ensure a comprehensive and adaptive approach to information security:
Establish a Clear Governance Structure — Begin by defining a clear governance structure with designated roles and responsibilities. Appoint a Chief Information Security Officer (CISO) or equivalent leadership to oversee the cybersecurity program and ensure accountability throughout the organization.
Conduct a Comprehensive Risk Assessment — This process involves evaluating the impact and likelihood of threats, allowing organizations to focus on mitigating the most significant risks to their information assets.
Develop and Implement Policies — These policies should cover data protection, access controls, incident response, and other critical aspects of information security.
Implement Security Controls — Choose controls that align with identified risks and compliance requirements, such as deploying technical measures to strengthen the organization’s overall security posture.
Prioritize Employee Training and Awareness — Well-informed staff members are essential for minimizing human-related risks and ensuring that the workforce is a proactive component of the organization’s security strategy.
Develop and Test Incident Response Plans — Regularly test these plans through simulations and exercises to ensure that the organization can respond swiftly and effectively to various scenarios.
Implement Continuous Monitoring and Improvement — Review and update cybersecurity measures based on monitoring outcomes, lessons learned from incidents, and changes in the threat landscape, embracing a culture of continuous improvement .
Create Your Own Cybersecurity Audit Checklist
Cybersecurity Governance Example
Now, what does cybersecurity governance look like in a practical situation?
Picture a small manufacturing company striving to safeguard its production processes from cyber threats. In the following example, learn how it employs a straightforward approach to cybersecurity governance tailored to prioritize the protection of its production data and machinery:
Assign Roles — The company picks a person to lead its cybersecurity efforts, in charge of making sure everything stays secure.
Check for Problems — They look for things that could cause trouble like someone trying to mess with their production machines or steal important data. They figure out what problems could happen and how bad they could be.
Make Rules — The company makes rules about how to keep its production data safe. These might include making sure only authorized people can access the machines and setting up passwords to protect key information.
Use Security Tools — They can also use special tools to stop bad things from happening. It’s like having guards and locks on all the doors to make sure only the right people can control the machines and access critical data.
Teach Everyone — They teach everyone who works at the company how to keep things safe. They show them how to recognize tricks that people might use, like clicking on suspicious emails, and explain why it’s crucial to protect the company’s production processes.
Be Ready for Problems — The company makes plans for what to do if something goes wrong. They practice what they would do if there was a big problem, like a cyberattack on their production systems, so they’re ready to fix it quickly.
Keep Watching — They use special tools to watch for anything unusual happening with their production machines or data. If something doesn’t look right, they can fix it before it causes any major issues in their manufacturing processes.
Enforce Cybersecurity Governance with SafetyCulture
Why use SafetyCulture?
It’s important to integrate cybersecurity governance efforts into a broader strategy that includes specialized tools, processes, and expertise. SafetyCulture (formerly iAuditor), as a workplace operations platform, helps streamline and improve safety and compliance processes within organizations. It can also support and enhance certain aspects of an organization’s cybersecurity governance program.
Using SafetyCulture, executives, risk management professionals, compliance officers, IT security managers, internal auditors, and organizations can do the following:
Gather information about the security posture of various departments or processes for risk assessments and compliance checks using customizable forms, checklists , and templates .
Report suspicious activities or potential security breaches using the incident and issues reporting functionalities. You can also ensure timely resolution by assigning corrective actions.
Ensure consistent implementation and monitoring of security controls and policies by creating and using cybersecurity checklists during audits.
Generate reports of conducted audits in various formats, including PDF, Excel, Word, or Weblink, and store them on SafetyCulture’s secure cloud .
Educate employees about security best practices, phishing awareness, and other relevant topics by conducting training sessions and awareness campaigns.
Improve visibility and access to cybersecurity policies and procedures by creating and sharing Heads Ups. You can also require employees to acknowledge receipt and understanding and notify them about security updates.
Assist in asset management and the implementation of security controls by maintaining an inventory of digital assets, devices, and software applications within the SafetyCulture platform.
Track the completion of security training, incident response times, and the status of compliance audits by monitoring KPIs related to cybersecurity using the Analytics dashboard.
Enhance the overall security ecosystem and ensure a holistic approach to cybersecurity governance by integrating the SafetyCulture platform with other relevant tools and systems.
Related articles
Information Technology
Security

A Guide to Global Data Privacy Day
Learn more about Data Privacy Day and the activities to celebrate it to ensure a more privacy-centric and efficient workplace.
Security
Information Technology

A Guide to Ensuring Cybersecurity for Manufacturing Organizations
A deep dive into what cybersecurity for manufacturing is, its importance, and the different ways for teams to enhance their cybersecurity framework.
Security
Information Technology

Phishing Attacks: How to Spot Them and Mitigate Them
A close look at what a phishing attack is, why it’s dangerous for companies, and the different ways teams can combat these attacks.