A Guide to Ensuring Cybersecurity for Manufacturing Organizations
Learn what cybersecurity for manufacturing is, why it’s important, and how to build a framework for it for your team.

Published 19 Dec 2025
Article by
7 min read
What is Cybersecurity for Manufacturing?
Cybersecurity for manufacturing refers to the digital hardware, software, and practices needed for protecting factories, production systems, and digital assets from threats that can disrupt operations or compromise sensitive data. It focuses on safeguarding control systems and supply chain networks from cyberattacks that could halt production or cause safety risks. Strong cybersecurity practices help manufacturers maintain uptime and ensure reliable, secure operations.
Importance
Cybersecurity is important in manufacturing because connected machines and industrial control systems create many points where attackers can break in. A single breach can halt production, damage equipment, or expose proprietary designs, resulting in costly downtime and lost revenue. Protecting these systems ensures continuous, safe, and reliable operations.
It also matters because manufacturing is a prime target for ransomware and supply chain attacks that exploit weak or outdated systems. Cyber incidents in this sector can ripple across partners, suppliers, and customers, affecting entire production networks. Hence the need for strong cybersecurity measures: to help safeguard data, maintain trust, and reduce the risk of disruptive threats.
Streamline Your Manufacturing Operations
Harness frontline insights, digital workflows, and seamless communication to boost efficiency and productivity across all manufacturing sites.
Challenges
While it is critical for maintaining safe and efficient operations, cybersecurity can come with many unique challenges, especially in the manufacturing industry. It’s important for teams to understand and prepare for these challenges beforehand to allow for smoother workflows.
IT-OT convergence
The convergence of Information Technology (IT) and Operational Technology (OT) systems creates unique challenges in manufacturing. This is because production equipment designed for stability is now connected to modern IT systems that change frequently. This blend of technologies can introduce security gaps, since OT devices often lack built-in protections found in traditional IT. As a result, manufacturers must secure systems that were never intended to be connected while keeping operations running without interruption.
Legacy equipment and flat networks
Legacy equipment and flat networks pose major risks to cybersecurity because many factories still rely on decades-old machines with outdated software and little to no security features. These devices often operate on flat, unsegmented networks, making it easier for attackers to move freely if they gain access. Upgrading or isolating these systems is difficult since they are essential to production and expensive to replace.
Large, distributed and diverse attack surface
A large, distributed, and diverse attack surface is common in manufacturing environments where factories use thousands of devices, sensors, and machines from different vendors. Each component creates a potential entry point, and many lack uniform security standards. Managing and securing such a varied ecosystem becomes especially challenging when production must stay continuous.
Supply chain and third-party risks
Supply chain and third-party risks are elevated in manufacturing because companies rely on numerous vendors for raw materials, specialized equipment, software, and maintenance, all of which can affect operations. Specifically, a weakness in any partner’s security can be exploited to infiltrate the manufacturer’s systems. This interconnectedness makes it harder to control risks and requires careful vetting and monitoring of all external parties.
Downtime costs and safety implications
Downtime costs and safety implications make cybersecurity especially critical because disruptions affect both revenue and worker safety. A cyberattack can halt machines, spoil products, or trigger unsafe operating conditions that endanger employees. Manufacturers must balance security measures with the need to keep equipment running safely and efficiently.
Best Practices to Ensure Manufacturing Cybersafety
It’s always best for teams to base their cybersecurity framework on the operations and needs of the business. This is why most teams have different frameworks than others, as there are different needs to consider.
That said, there are some best practices that will apply to most manufacturing organizations, which include the following:
Adopt a structured framework
A structured cybersecurity framework or governance helps manufacturers follow consistent, proven security practices tailored to industrial environments. Frameworks like NIST CSF or IEC 62443 offer guidance for protecting both IT and OT systems without disrupting operations. This approach ensures teams can prioritize risks, standardize controls, and improve security maturity over time.
Asset inventory and risk assessment
Regularly monitoring risks and asset inventories is essential because factories contain a mix of legacy machines, modern Internet of Things (IoT) devices, and critical control systems. Knowing what equipment exists, how it connects, and what vulnerabilities it carries allows teams to focus on the highest-risk areas. Having this visibility helps manufacturers prevent blind spots and strengthen protection around their most critical assets.
Network segmentation and isolation
Network segmentation and isolation reduce risk by separating vulnerable OT systems from corporate IT networks and external access points. This limits how far an attacker can move if they breach one area, protecting production equipment from broader compromise. Segmentation also allows manufacturers to apply security controls without interrupting operations.
Secure devices
Securing cybersecurity devices, particularly OT and IoT devices, is vital because many industrial machines lack native security features and may run outdated firmware. Applying strong authentication, regular patching, and continuous monitoring helps compensate for these weaknesses. This ensures that connected equipment remains protected even when it cannot be easily upgraded or replaced.
Supply chain and third-party security
Supply chain and third-party security is critical because manufacturers rely on vendors for hardware, software, maintenance, and specialized components. Ensuring partners follow strong security standards reduces the risk of attackers entering through external systems or compromised products. Ongoing monitoring and clear requirements help safeguard the entire production ecosystem.
Building a Cybersecurity Framework for Manufacturing
Cybersecurity is critical in manufacturing, but setting up a framework for it can be a tall task for many teams. To help, here’s a step-by-step guide to how teams can build an effective cybersecurity framework for their manufacturing operations:
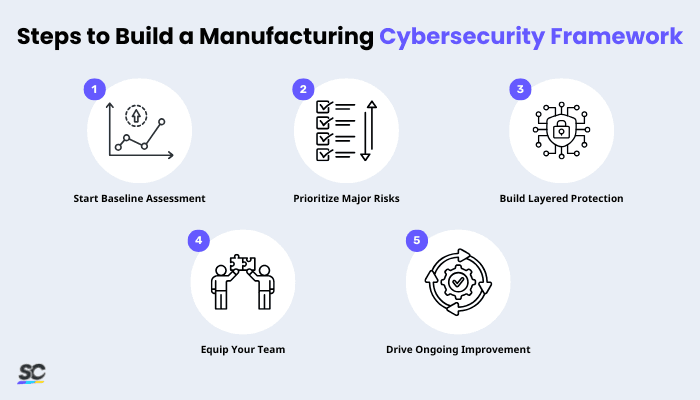
Steps to Build a Manufacturing Cybersecurity Framework
Step 1: Conduct a baseline assessment
A baseline assessment or cyber health check helps manufacturers understand the current state of their cybersecurity by identifying assets, vulnerabilities, and existing controls across both IT and OT systems. Digital checklists and forms make this process more accurate and repeatable by standardizing inspections, ensuring nothing is overlooked, and making it easier to track issues. With a clear starting point, teams can make informed decisions about where to focus their efforts first.
Step 2: Prioritize high-impact risks
After conducting a baseline assessment, it’s time to identify and prioritize cybersecurity risks to manufacturing operations. Prioritizing high-impact risks allows manufacturers to address the threats most likely to disrupt production, compromise safety, or expose sensitive data. Because factories have complex environments, focusing on the biggest risks prevents resources from being spread too thin. This targeted approach helps strengthen protection where it matters most.
Step 3: Build layered defense
Building a layered defense means using multiple security controls such as network segmentation, access management, endpoint protection, and OT monitoring. Together, alongside risk assessments, these help create overlapping protection for critical systems. This approach is especially important in manufacturing, where single points of failure and cyber risks can shut down production. Layering helps ensure attackers cannot easily bypass defenses, even if one control fails.
Step 4: Equip the people
Equipping the people focuses on training employees, technicians, and operators to recognize threats, follow secure practices, and respond correctly to incidents. Manufacturing environments involve many staff members who interact with machines daily, so human error from lack of training and incorrect gear can quickly lead to operational disruptions. Clear procedures, awareness programs, and role-specific guidance help reduce these risks.
Step 5: Embed continuous monitoring and improvement
Embedding continuous monitoring and improvement into daily operations ensures that cybersecurity remains effective as new threats, devices, and processes emerge. Manufacturers benefit from real-time monitoring tools and ongoing audits that help identify anomalies before they escalate. By reviewing performance regularly and updating controls, organizations can maintain a strong and adaptable security posture.
Enhancing Cybersecurity for Manufacturing with SafetyCulture
Why use SafetyCulture?
SafetyCulture is a mobile-first operations platform adopted across industries such as manufacturing, mining, construction, retail, and hospitality. It’s designed to equip leaders and working teams with the knowledge and tools to do their best work—to the safest and highest standard.
Streamline processes, eliminate defects, enhance equipment utilization, and build a dependable infrastructure with SafetyCulture. Strive for overall equipment effectiveness to boost competitive advantage, foster sustainable growth, and deliver long-term value.
✓ Save time and reduce costs
✓ Stay on top of risks and incidents
✓ Boost productivity and efficiency
✓ Enhance communication and collaboration
✓ Discover improvement opportunities
✓ Make data-driven business decisions
Related articles
Information Technology
Security

A Guide to Global Data Privacy Day
Learn more about Data Privacy Day and the activities to celebrate it to ensure a more privacy-centric and efficient workplace.
Security
Information Technology

Phishing Attacks: How to Spot Them and Mitigate Them
A close look at what a phishing attack is, why it’s dangerous for companies, and the different ways teams can combat these attacks.
Security
Information Technology

Cyber Health Check: Strengthening Your Digital Defenses
Learn what a cyber health check is, why it’s crucial to your business, and how to conduct one effectively to protect against cyber threats.